Cisco Catalyst 1200-8T-D Smart Switch-SSH and Radius Configurations

One of the first steps when deploying a new network device is to configure it for remote access. In this post, I’ll walk you through the process of setting up SSH and RADIUS on a Cisco Catalyst 1200 switch using the CLI. While these configurations can also be performed through the web console, we’ll focus on the CLI approach here.
Configuring SSH
All the commands listed below are slightly different than traditional IOS but are fairly straightforward. Enabling SSH on this switch is as quick and easy. In other Cisco platforms, you often have to add a domain name, generate keys, create users, and then apply line settings. With the Catalyst 1200, we’ll start by simply entering:
ip ssh serverOur next step would typically be configuring the vty lines for ssh. However in this case, instead of vty lines, the Catalyst 1200 offers lines for each protocol:
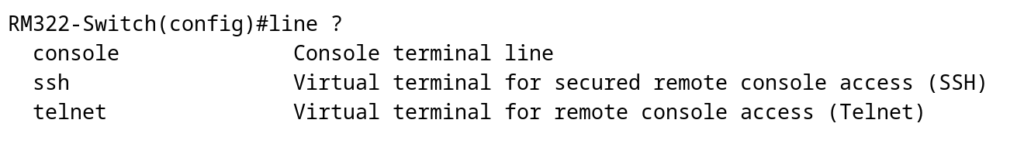
Options within the ssh line are somewhat similar to what you might be familiar with seeing in traditional IOS:
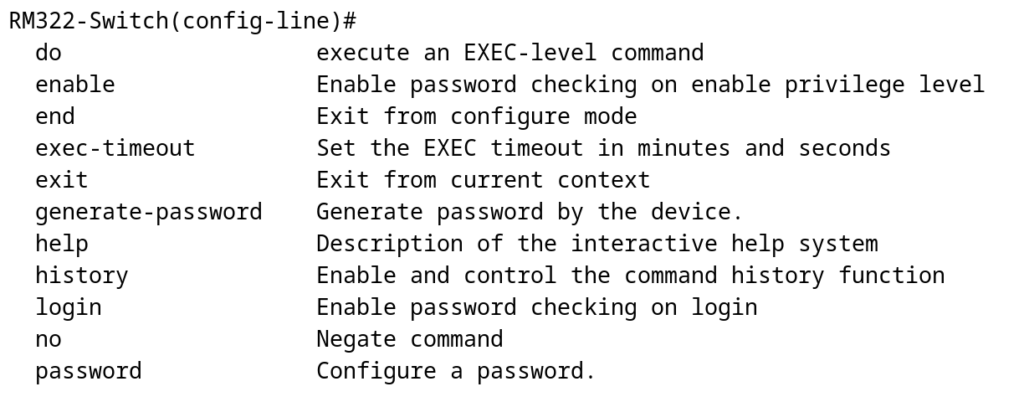
One noteable configuration missing is the access-class option. In other Cisco platforms, this allows us to associate an access control list, so that we can filter what IP addresses can remotely access our device. Instead of having a “per line” access-class, the Cisco Catalyst 1200 uses a management access-class that allows filtering on all remote access types. Here’s an example of my setup where I create an ACL that allows ssh and https from a few of my subnets and then apply the access-list to the management access-class:
management access-list MGMT-ACL
permit ip-source 192.168.100.0 mask 255.255.255.0 service ssh
permit ip-source 192.168.100.0 mask 255.255.255.0 service https
permit ip-source 192.168.104.0 mask 255.255.255.0 service ssh
permit ip-source 10.10.10.1 service ssh
!
management access-class MGMT-ACLDisclaimer
Its worth noting that because this switch only allows a single management access-class option, you’ll want to have a console cable ready in case you make a mistake. A typo here could lock you out of both ssh and https access.
Configuring RADIUS
Our next step would be to assign authentication options to our line. I’ll be using radius for network users but the switch supports several options. To start with radius configuration, I first need to specify at least one radius server. Unlike my problems with SNTP I was able to specify servers via hostname. Radius server configuration is pretty straightforward and looked like this for me:
radius-server host radius1.rm322.com key R@D1uSk3Y
radius-server host radius2.rm322.com key rA|)iU5|<ey Once your servers are configured, they’ll actually look like this in your configuration:
encrypted radius-server host radius-1.rm322.com key <hash>
encrypted radius-server host radius-2.rm322.com key <hash>The next step will be to configure aaa settings. My configuration required a line to specify login and enable settings. I chose to name my configuration “RAD” and set login authentication to use radius with local login as a fall back. I then set enable authorization to none under the same “RAD” name. I chose to set enable to none because when I tried setting enable authorization to radius, I was unable to authenticate with my servers. I also prefer to not have to provide my password twice or a separate enable password. In IOS I set my ssh lines to immediately dump me into privilege 15 but was unable to find a similar method with this device. My configuration for the above looked like this:
aaa authentication login RAD radius local
aaa authentication enable authorization RAD noneFinally, I had to configure my ssh lines to use the aaa profiles I just created. I completed this with the following commands:
line ssh
login authentication RAD
enable authentication RADVerifying the Configuration
To check our configurations we can attempt to remotely access our switch from an IP address that matches our MGMT ACL and an IP address that doesn’t. Here you’ll see the management ACL prevent an address that doesn’t match any permit statements as well as a successful login from a radius user on approved address space:
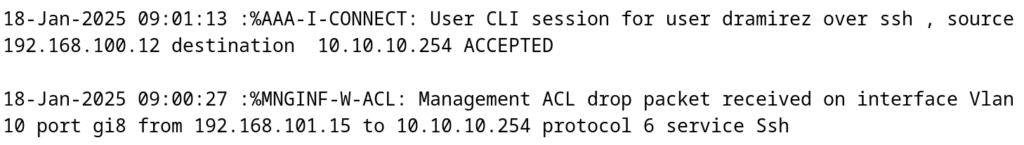
Some common troubleshooting and validation commands you can use for ssh and radius are:
- show ip ssh
- show users
- show logging
- show radius-servers
- show authentication methods
Configuring SSH and RADIUS on the Catalyst 1200 is slightly different from traditional IOS, but the process is quick and straightforward. Thanks for reading! If you have any questions or tips about configuring the Catalyst 1200, feel free to reach out!