Migrating/Updating my TinyDB MAC API – NGINX and HTTPS
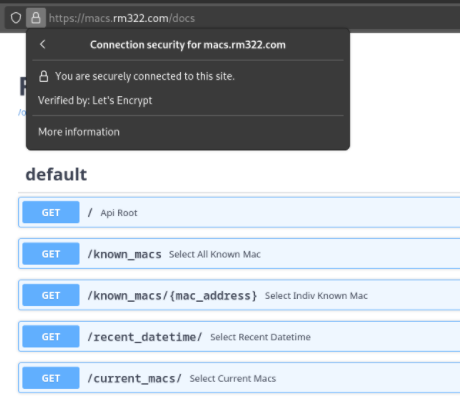
Now that I have a functioning app, I’d like put a reverse proxy on it so that I can limit what addresses can reach it and put an SSL certificate in front of it. To do this I’ll be using NGINX and Let’s Encrypt.
Lets Encrypt offers several ways to obtain a certificate for your domain. In my environment, the DNS challenge works best for me. Your environment may vary, but ultimately the DNS challenge requires a TXT record to be created to validate domain ownership. I start the process by issuing the following command:
certbot certonly --manual --preferred-challenges=dns -d macs.rm322.comOnce this is done, certbot will provide you the required information to create your TXT record:
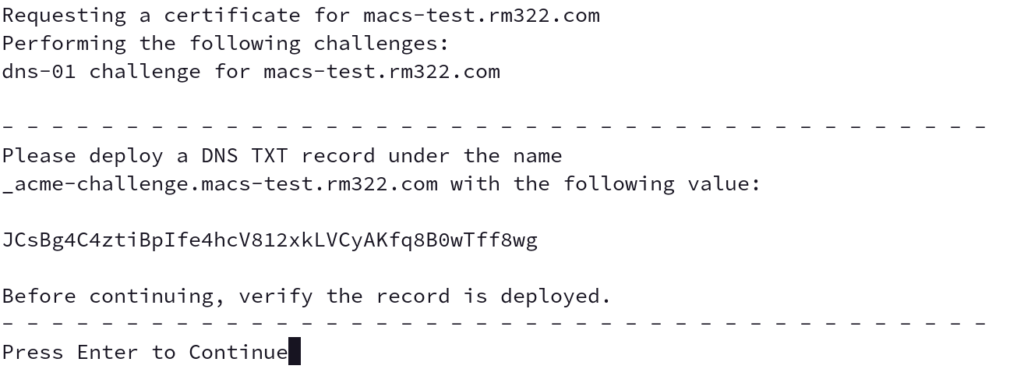
Once the TXT record is created, simply hit enter, and if the record was created properly, you’ll be issued a certificate.
NGINX allows you to create individual configuration files under /etc/nginx/conf.d. My reverse proxy has several configuration files that correspond to each individual website. I like to name mine using the following standard: ##_<domain-name>.conf. Below is my configuration file along with explanations:
upstream macs {
server 192.168.10.10:8000;
}
server {
listen 80;
server_name macs.rm322.com;
return 301 https://macs.rm322.com;
}
server {
listen 443 ssl;
server_name macs.rm322.com;
allow 192.168.0.0/24;
deny all;
ssl_certificate /etc/letsencrypt/live/macs.rm322.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/macs.rm322.com/privkey.pem;
location / {
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_pass http://macs;
}
}upstream: Here I put my backend server or servers along with the port my app is using.
server: Broken into two parts: an 80 redirect to 443 and a 443. The 80 redirect is straightforward; provide a 301 redirect to the client and direct them to the HTTPS site. The 443 is broken into several parts:
- server_name: Whatever your certificate/DNS will be set to.
- allow/ deny: List allowed and denied addresses here.
- ssl_cert/ssl_cert_key: Location of the certificate.
- location /: Apply the below configurations to all locations.
- proxy_set_header: Send Host and X-Forwarded-For Headers to the app.
- proxy_pass: Send traffic to the the upstream location we annotated earlier.
And just like that, we have a certificate sitting in front of our application.
